Many of our customers and readers are undoubtedly users of social networking sites like MySpace, Twitter, and
Facebook
. I'd like to remind our friends and readers of the importance of actually understanding some recent changes to the privacy settings in Facebook. If you simply clicked "Next...Next...Finish" and "I Agree" when this week's notice popped up in Facebook, you should read on.
Facebook introduced changes in their privacy settings this week under the guise of making these settings more customizable and granular for their users. I tend to think there are other reasons, but we'll leave that discussion to the dozens of other blogs and media outlets that are beating that drum this week. My focus in this posting is simply to make Facebook users (current and future) aware that by default there is very little privacy when using Facebook.
First, let's talk about what kinds of data you might have within your Facebook account.
First Name
Last Name
Phone Number
City of Residence (this could also be the city in which you were born)
State of Residence (this could also be the state in which you were born)
Birthdate
Employer/School
Sex
Religious views
Political views
Email address
Photos of you
Videos of you
Your daily activities and/or geographic location (depending on how much you offer in your status updates)
Job title
Relationship status (and the name of your significant other, if applicable)
Favorite movies, TV shows, music, books, etc
etc.
etc.
etc.
Now that you see the list above all in one place, doesn't seem like an excessive amount of information to be giving away? It does to me. I can't see why there is a legitimate need to share this amount of information with so many people. But then I guess that depends on your personal thoughts on the subject and, as we'll see later in this post, how you have your privacy settings configured on Facebook.
Who sees this stuff? That also depends on how you have your
Facebook privacy
settings configured. But first and foremost you should understand that Facebook's default and recommended settings let the whole world see this information. Keep in mind, Facebook isn't just an online community of your peers and friends. It's also a treasure trove of information for those seeking to
steal your identity
or tailor their advertising to you. Or to send you spam. Or to steal your identity. Did I mention
identity theft
?
Who has an interest in this kind of information?
Identity thieves
. Advertisers.
Spammers
. Your ex-girlfriend/boyfriend stalker. The guy across town who wants your new LCD TV and would like to know when you're out of town (remember, you told him you were in Cancun?). Your employer (you know, to see what you're REALLY doing when you call in sick).
Alright, so I've scared a few of you, open the eyes of some of you, and lost the rest of you. Well pay attention, the good stuff is up next. Let's take a good look at the settings that Facebook "recommends" that you accept.
Click on
Settings at the top of the Facebook page and then select
Privacy Settings and you'll see a page like this:
 The first area to consider is the Profile Information section. This will show you the details of all the things you're sharing, and with whom. Things like birthday, relationship status, and employer can be found here. I suggest setting all of them to Only Friends. You can even set them to Only Me or to specific users by selecting the Customize option.
The first area to consider is the Profile Information section. This will show you the details of all the things you're sharing, and with whom. Things like birthday, relationship status, and employer can be found here. I suggest setting all of them to Only Friends. You can even set them to Only Me or to specific users by selecting the Customize option.
The Contact Information section allows you to specify who can view your phone number, email addresses, website url, IM screen names, etc. These settings can also be set to be available to a many or as few people as you like, but I suggest that they be restricted to Only Friends at a minimum.
The next section is one that I think is widely overlooked. The Applications and Websites area is one that can protect or expose a ton of your personal information. In some cases, this exposure can take place without your knowledge or participation.
For starters, click on the Learn More button next to the What You Share section. Read it. Understand it. Please don't take it lightly. When you use applications in Facebook, you are agreeing to let the developers of those applications have access to your personal information to do with it whatever they wish. Photos, personal data, email addresses, birthdates, children's names, etc. All of these things (and more) are surrendered when you use a third party application within Facebook. The What You Share section will help you understand this. Read it. Understand it. Did I mention identity theft? Yeah, see, you have no idea who wrote those applications you're using. Quizzes? Games? Send a friend a drink or a gift? Yeah, those are the applications I'm talking about. You have no idea who wrote them, why they wrote them, and what parts of your personal data they're taking for their own use (or to sell to someone else).
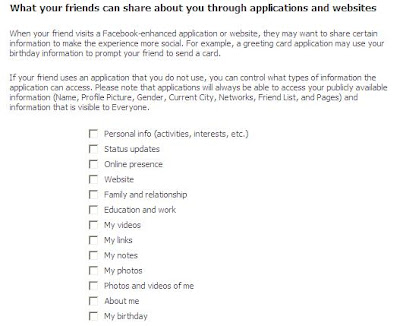
Another good place to keep an eye on is the What Your Friends Can Share About You. Click on the Edit Settings button for this section and find all the ways (and there are many) that someone you're friends with on Facebook can agree to give away YOUR personal data. That's right, you don't even have to give away your own personal information. An unsuspecting friend of yours can do it for you, saving you the trouble. Nice, huh? Do yourself a big favor...go to this section and un-check every box you see. There is no reason that any of your friends' activities should result in the exposure of your personal information. Can you say identity theft?
The last two sections of the Applications and Websites area will allow you to view and edit applications you have blocked or edit which invitations you have previously chosen to ignore. These areas are pretty self explanatory (by now you're getting pretty good at this stuff anyway, huh?).
So, are you a little more paranoid than you were at the beginning of this post? Good, then my work is done here. Remember, privacy is a right that must be guarded and protected. Don't give away personal information unless it is absolutely necessary. And when it comes to Facebook, it's never necessary.








